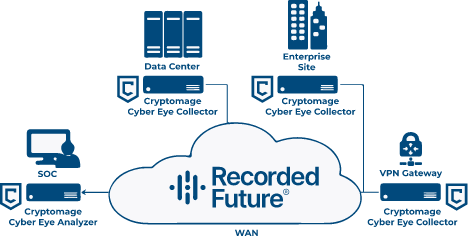
Cryptomage Cyber Eye™
Network Detection and Response

Types of detected cyberattacks
Hidden network communication
Botnet communication
Malware
0-day attacks
DDoS attacks
Sectors
Cryptomage in numbers
advanced code lines
proprietary
modules
days takes to detect attack
without our probe
types of detected
cyberattacks
Modules
Threat detection
Threat detection provides deep inspection of every single network packet, including transported data, with:
- Network protocol discovery and validation – easily check unknown and hidden protocols
- Machine learning algorithms – to score traffic risk proactively.

Event management
Event management with full SIEM, SOAR and NGFW integration and export thresholds
- Risk scoring of each event and host – effective triaging of threats
- Built-in analytic tools and charts – inform and guide ongoing event management
- Configurable event triggers – giving you control over certain packets or events when needed

Network monitoring
Network monitoring with proprietary flow metadata formats that go beyond traditional network flow analysis:
- Protocol behavior and anomaly statistics – wider understanding of traffic flow and behavior
- Passive mode option – operations don’t interfere directly with the network traffic

Forensics
Forensics to better measure the ratio of security events against the source of traffic:
- Extraction of high-risk network traffic – easy to analyze and focus on specific threat levels
- Storage of processed traffic metadata in extended format – faster trend analysis
GDPR
Personal data leak detection
- Inspection of network packets to detect transmission of personal data such as ID numbers, social security numbers, and bank account numbers
- Report generation for the Data Protection Officers
What makes us different
Cryptomage Cyber Eye™ offers unique approach to network traffic analysis, with a combination of protocol behavior, packet analysis, and host communications behavior analysis. While most security solutions focus only on user and host behavior, Cryptomage Cyber Eye™ also incorporates unusual low-level network behavior.
This way, the solution analyzes network protocol and host activity with our groundbreaking network steganography expertise. This includes the detection and prevention of unknown or hidden network traffic, communication, and information/data, such as when a TCP/IP protocol has been intentionally modified to allow illegal botnet operations to occur.
While Cryptomage Cyber Eye™ is constantly evolving, armed with AI and machine learning capabilities, it is also designed to integrate and interact with other security solutions to increase threat detection. This means you can combine our unique network analysis capabilities with other security tools to achieve even greater levels of threat detection.